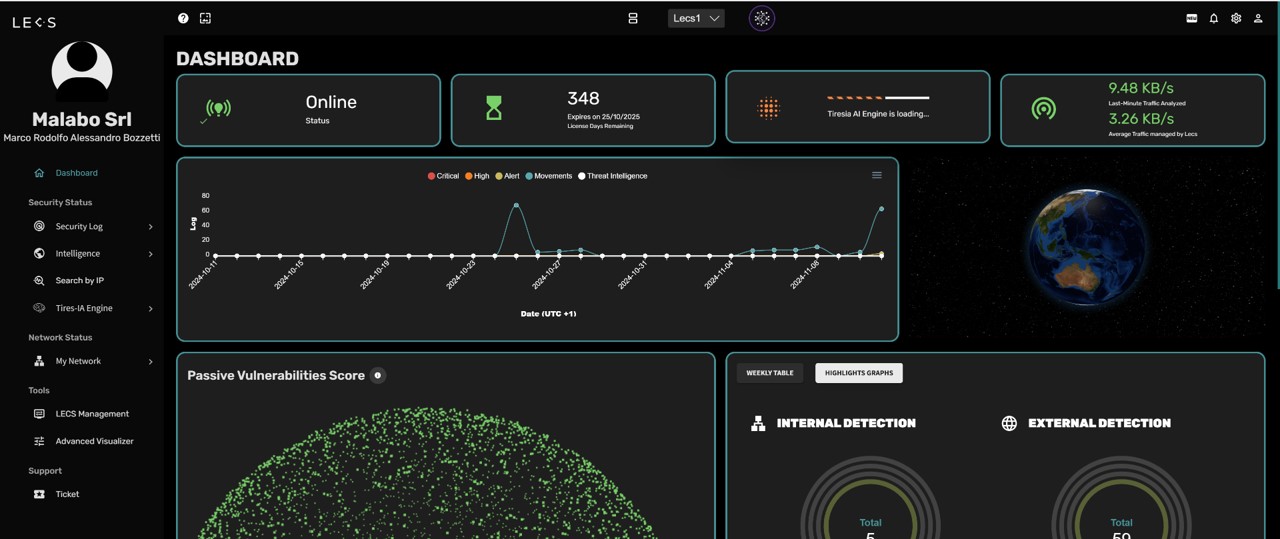
What is LECS?
LECS is the world first innovative Plug & Play cybersecurity appliance that protects any local area network (LAN) , infrastructure and industrial plants from the most dangerous cyber attacks and threats.
LECS is a complementary IPS/NDR (Intrusion Prevention System / Network Detection and Response) device that complements and adds a significant security layer to your existing measures, thus significantly improving your Cyber Security posture.
- NDR systems build models of normal behavior by continuously analyzing north/south network traffic crossing the enterprise perimeter, as well as east/west lateral traffic, and then use these models to identify anomalous or suspicious traffic patterns. They also incorporate incident response capabilities, such as blocking suspicious traffic. They also incorporate incident response capabilities, such as blocking suspicious traffic. This may include automatically updating firewall rules to block suspicious traffic or providing capabilities to aid in incident and threat/risk investigations. IPS systems perform prevention activities on incoming traffic, blocking suspicious traffic, and also referring, in the LECS implementation, to the NDR traffic models.
LECS is a plug&play system as it does not need to be configured to be installed, but, once connected to the network, it automatically recognizes the context and self-configures, integrating with the other digital security tools present and connecting in polling with 4C, Control Center CyberEvolution in Cloud, the LECS control center in the cloud, to perform various functions.
LECS uses a chain of 3 different AI (Artificial Intelligence) engines to analyze a single threat, thus being able to perform advanced detection of dangerous and invisible lateral movements.
How it works
Connected to the mirroring port of a switch or a network router (see example in the figure below), LECS analyzes all the traffic of the local network and the incoming and outgoing traffic on the Internet connections, and once an anomaly is detected, it classifies it and acts based on the degree of severity with a modulated response to the potential attack.
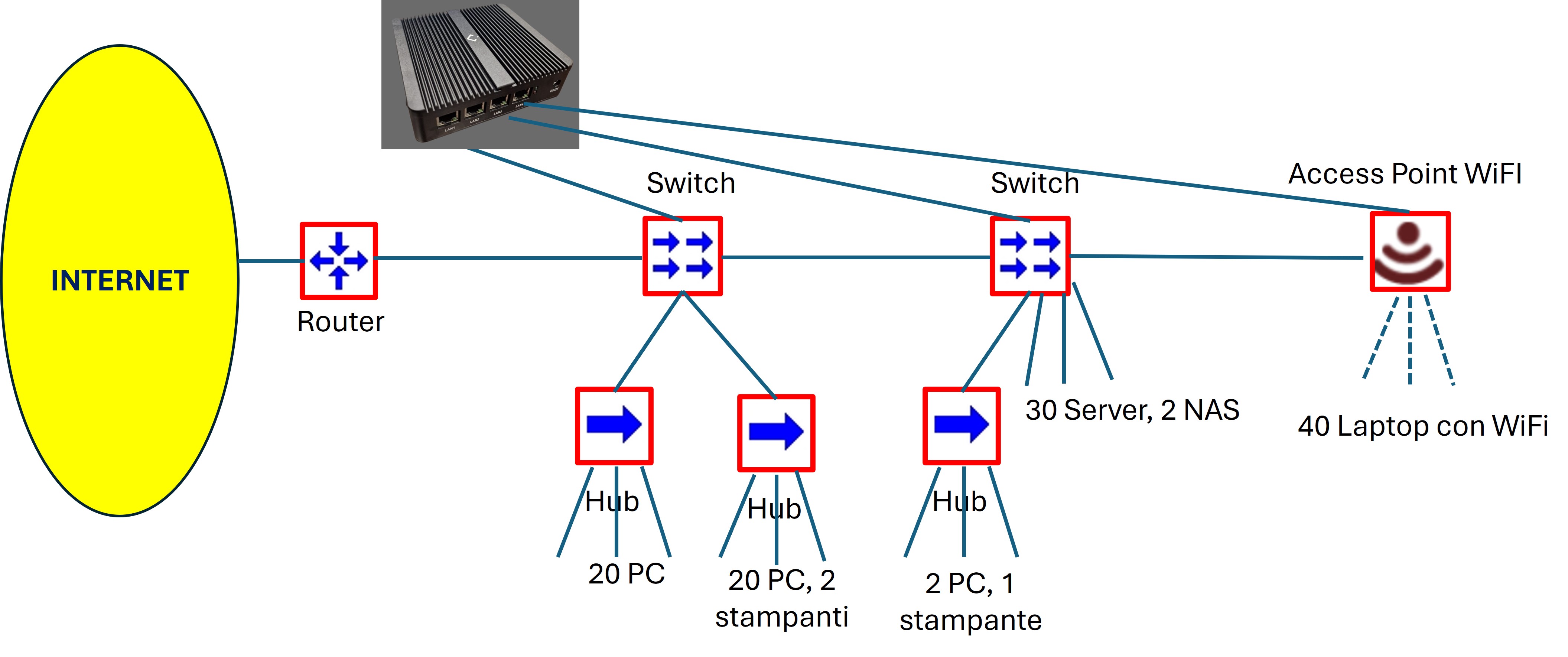
LECS is based on 3 AI engines that are the cornerstone of its entire operation: Specto, Raises and Tiresia. The three AI systems with their machine learning algorithms work synergistically and in parallel to protect an entire network segment, performing detection and classification of anomalies on network traffic, acting with targeted countermeasures and responses in cases of critical threats and performing an intelligent prediction that provides an update feedback based on the latest statistics detected.
The operating phases of a LECS are:
- CHECK & CONNECT LECS: after having positioned it on a mirroring port of a "strategic" switch of the network infrastructure, LECS self-configures (plag&play) and becomes a component, host, of the network, and begins its passive monitoring, which does not impact network performance;
- TRAP & DETECTION ANALYSIS: during the continuous and real-time monitoring of network traffic, LECS identifies and analyzes possible threats in real time, classifying them based on the severity of the possible impact;
- IMPACT ISOLATION RESPONSE: in case of detection of a high-impact threat, LECS intervenes by creating packets that mix with those of the identified malicious traffic and therefore blocking the threat at the protocol level; in extreme cases, LECS blocks the power supply of the switch to which it is connected;
- INSPECTION & RECOVERY NETWORK: following the above intervention, LECS LECS restores the network connection, checks for the presence of further threats and, thanks to the Tiresia algorithm, learns and parameterizes the threat data.
LECS provides an advanced network control and monitoring:
- Check the statuts of any online devices, thanks to network behavior analysis and automatic updates.
- 24/7 monitoring, device protection, attack prediction, active countermeasures.
- Advanced Multi-Tenant Control for IT/OT (Operational Technology: IoT, IIoT, SCADA, robotics, etc.) systems.
False positives and negatives
False positives and false negatives have always been a very serious problem for threat detection systems. Thanks to the internal detection systems that perform machine learning action, LECS carries out a strong Auto Reduction for both.
- To date, after more than 4.5 years in production environments, LECS statistically has reported no false positives for critical levels.
LECS Notarization
LOG events with private blockchain for threat traceability, certification, regulations and insurance purposes.
LECS Recovery
In case of malfunction or disaster of the appliance, if it concerns the hardware the entire device must be replaced, if it concerns only the software, it can be easily recovered by a specific USB stick that is always associated to the appliance.

Why buy LECS
- LECS is born with a clear objective: to make computer security more accessible, simpler and more effective.
- LECS provides a strong enhancement of cyber security among local devices in the local area networks (PCs, servers, storage, network units, etc.) and connected to the Internet: thanks to the 3 AI engines, LECS identifies at the network level already known and unknown malicious codes (the so-called zero-days, which firewalls and anti-malware cannot detect), and/or unusual behavior of the different local devices (with the AI engines it records the behavior of each unit over time), and intervenes autonomously to render the threats harmless.
- LECS provides a wide response capacity, both preventive during the reconnaissance phases and responsive during lateral and exploit movements.
- LECS obtains an optimized dynamic monitoring system that analyzes and responds to thethreat by biunivocally combining all possible types of detection.
- LECS is a "plug & play" device that autonomously self-configures when connected to the local network in which it must operate, without the need for human intervention.
- LECS uses a natural language interface in its dashboard, that extracts the most important data thanks to Machine Learning.
- LECS is not directly attackable, unlike other configurable systems such as firewalls, antivirus, etc. since:
- Its software cannot be accessed in any way, neither locally nor remotely;
- It only allows outgoing traffic to the Control and Management Center;
- It does not require the installation of specific code (agent) on each unit it controls.
- LECS is constantly evolving and it is continuously and securely updated.
- LECS has a very competitive price, in particular if compared to similar products such as DarkTrace, Vectra, ThreatBook, OpenStack appliances.
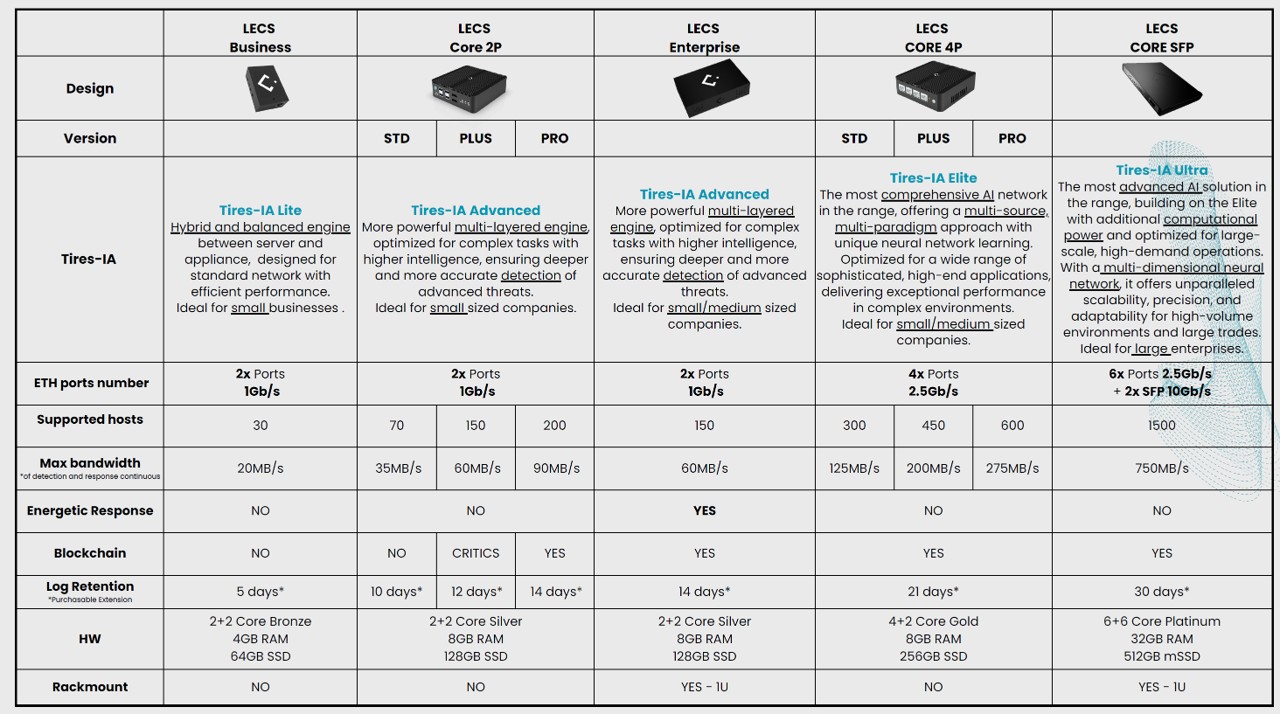
- LECS provides a wide range of products to cover from very small local networks (up to 30 hosts) to large ones (up to 5000 hosts): see the following comparison table.
- LECS and its designer-manufacturer company have achieved the following important certifications:
- ISO 9001: international quality management standard.
- ISO 27100: assurance of compliance with information security requirements.
- NIST Framework 1.1: conformità ai requisiti del National Institute of Standards and Technology.
- NIST Framework SP800: Advanced Security for Critical Infrastructure.
- NIS2 Directive: Compliance Support for Critical Infrastructure Management.
- ACN Certification, the National Cybersecurity Agency - coming soon
- LECS and its designer-manufacturer company are:
- Winners CDP Forward Factory 2022
- Winners at KickStart Global @Zurich
- Winners of the Italian Lifestyle Nana Bianca acceleration programme
- Among the best start-ups at the Enterprise Europe Network @EU PRAGUE
- TIM Cyber Challenge Finalists
- Partner EIT Manifacturing
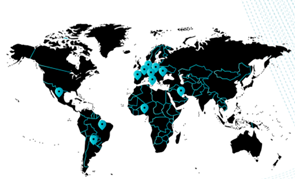
LECS is now It present in several (19) countries, not only in Europe, as shown in the map.
Current LECS products
For more information, for a live demonstration and for a quote please contact

